Has Nintendo Switch already been hacked?
Old browser exploit compromises new console.
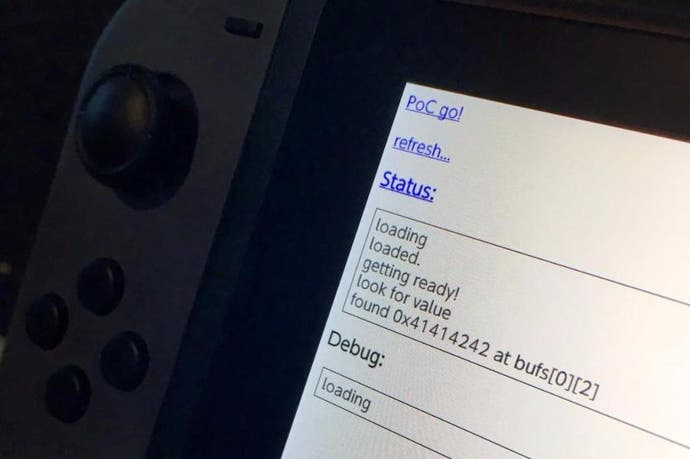
Mere weeks after its release, hackers have already begun to peel back layers of Nintendo Switch's security - with a simple browser exploit now available. The exploit was revealed by iOS hacker qwertyoruiop, who claims he did nothing more than to very simply re-purpose a hack originally used to 'jailbreak' Apple iOS 9.3 devices. Later on, another hacker - LiveOverflow - confirmed that the exploit works and a proof of concept was publicly released.
It's all rather fascinating bearing in mind that the Switch isn't supposed to ship with a fully functional browser at all. However, some kind of HTTP access is required to access WiFi networks that require registration - and only then does the browser make itself known. Tools already exist to hijack this tool and divert it to other websites and even rudimentary video playback is supported.
The browser is based on widely-used Webkit technology, but it turns out that Nintendo has used an older, easily exploitable codebase that has since been patched. The end result is that the first line of protection against hackers has now fallen, and hackers should be able to probe the Switch's operating system for further exploits much more easily.
However, it is important to stress that while significant, the extent of the exploit is limited - Webkit hacks (and there have been many across the years, across several console platforms) only allow for access to 'userland' - unofficial code can be executed, but without any tools to generate code, there is no real benefit right now. Low-level access is also non-existent, so this hack alone will not lead to custom firmware or piracy.
However, with a user-level exploit, hackers will be free to examine the Switch's operating system much more closely and to further understand how it operates and by extension, how it may be compromised.
It's likely that Nintendo will respond by implementing the required patches to bring the Webkit browser applet up to its latest version, eliminating this well-known exploit. With a patched firmware in place, it will make more fully-formed hacks more difficult to deploy, but the damage is done in terms of allowing hackers any kind of access to the machine. While virtually useless to end-users, this hack will prove invaluable to researchers attempting to figure out how Switch works, and how to further exploit it in the future.
And with that in mind, it's surprising that Nintendo shipped Switch with an easily exploitable browser. The platform holder has often fallen foul of browser-based exploits on previous hardware, and the particular hack used here, designated CVE-2016-4657, seems to have been refashioned into an Apple-specific 'jailbreak' in early December 2016, leaving Nintendo with months to ensure that the browser used in Switch was fully up to date - and not subject to a vulnerability that was deployed on literally millions of iOS devices.